Syntax
dce_iface:<uuid>[, <operator><version>][, any_frag];
uuid = hexlong '-' hexshort '-' hexshort '-' 2hexbyte '-' 6hexbyte
hexlong = 4hexbyte
hexshort = 2hexbyte
hexbyte = 2HEXDIGIT
operator = '<' | '>' | '=' | '!'
version = 0-65535
Examples
dce_iface:4b324fc8-1670-01d3-1278-5a47bf6ee188;
dce_iface:4b324fc8-1670-01d3-1278-5a47bf6ee188, <2;
dce_iface:4b324fc8-1670-01d3-1278-5a47bf6ee188, any_frag;
dce_iface:4b324fc8-1670-01d3-1278-5a47bf6ee188, =1, any_frag;
This option is used to specify an interface UUID. Optional arguments are an interface version and operator to specify that the version be less than ('<'), greater than ('>'), equal to ('=') or not equal to ('!') the version specified. Also, by default the rule will only be evaluated for a first fragment (or full request, i.e. not a fragment) since most rules are written to start at the beginning of a request. The any_frag argument says to evaluate for middle and last fragments as well. This option requires tracking client Bind and Alter Context requests as well as server Bind Ack and Alter Context responses for connection-oriented DCE/RPC in the preprocessor. For each Bind and Alter Context request, the client specifies a list of interface UUIDs along with a handle (or context id) for each interface UUID that will be used during the DCE/RPC session to reference the interface. The server response indicates which interfaces it will allow the client to make requests to - it either accepts or rejects the client's wish to bind to a certain interface. This tracking is required so that when a request is processed, the context id used in the request can be correlated with the interface UUID it is a handle for.
hexlong and hexshort will be specified and interpreted to be in big endian order (this is usually the default way an interface UUID will be seen and represented). As an example, the following Messenger interface UUID as taken off the wire from a little endian Bind request:
|f8 91 7b 5a 00 ff d0 11 a9 b2 00 c0 4f b6 e6 fc|
must be written as:
5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc
The same UUID taken off the wire from a big endian Bind request:
|5a 7b 91 f8 ff 00 11 d0 a9 b2 00 c0 4f b6 e6 fc|
must be written the same way:
5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc
This option matches if the specified interface UUID matches the interface UUID (as referred to by the context id) of the DCE/RPC request and if supplied, the version operation is true. This option will not match if the fragment is not a first fragment (or full request) unless the any_frag option is supplied in which case only the interface UUID and version need match. Note that a defragmented DCE/RPC request will be considered a full request.
Note:
Using this rule option will automatically insert fast pattern contents into
the fast pattern matcher. For UDP rules, the interface UUID, in both big and
little endian format will be inserted into the fast pattern matcher. For TCP
rules, (1) if the rule option flow:to_server|from_client is used, 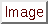 05 00 00 05 00 00 will be inserted into the fast pattern matcher, (2) if the rule option
flow:from_server|to_client is used,
will be inserted into the fast pattern matcher, (2) if the rule option
flow:from_server|to_client is used,  05 00 02 05 00 02 will be inserted into the
fast pattern matcher and (3) if the flow isn't known, will be inserted into the
fast pattern matcher and (3) if the flow isn't known,  05 00 05 00 will be inserted
into the fast pattern matcher. Note that if the rule already has content rule
options in it, the best (meaning longest) pattern will be used. If a content
in the rule uses the fast_pattern rule option, it will unequivocally be used
over the above mentioned patterns. will be inserted
into the fast pattern matcher. Note that if the rule already has content rule
options in it, the best (meaning longest) pattern will be used. If a content
in the rule uses the fast_pattern rule option, it will unequivocally be used
over the above mentioned patterns.
|