 port
port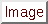 port
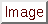
port![$> <...>] \}$](img8.png)
This option specifies the source ports that the DNS preprocessor should inspect traffic.
Alert on Obsolete (per RFC 1035) Record Types
Alert on Experimental (per RFC 1035) Record Types
Check for DNS Client RData TXT Overflow
By default, all alerts are disabled and the preprocessor checks traffic on port 53.
The available configuration options are described below.
 port
port port
port![$> <...>] \}$](img8.png)
This option specifies the source ports that the DNS preprocessor should inspect traffic.
Alert on Obsolete (per RFC 1035) Record Types
Alert on Experimental (per RFC 1035) Record Types
Check for DNS Client RData TXT Overflow
The DNS preprocessor does nothing if none of the 3 vulnerabilities it checks for are enabled. It will not operate on TCP sessions picked up midstream, and it will cease operation on a session if it loses state because of missing data (dropped packets).