 port
port port
port![$> <...>] \}$](img8.png)
This is how the user configures which ports to decode as FTP command channel traffic. Typically port 21 will be included.
During initialization, this option causes the preprocessor to print the configuration for each of the FTP commands for this server.
![$\{ cmd [cmd] \}$](img10.png)
The preprocessor is configured to alert when it sees an FTP command that is not allowed by the server.
This option specifies a list of additional commands allowed by this server, outside of the default FTP command set as specified in RFC 959. This may be used to allow the use of the 'X' commands identified in RFC 775, as well as any additional commands as needed.
For example:
ftp_cmds { XPWD XCWD XCUP XMKD XRMD }
 number
number
This specifies the default maximum allowed parameter length for an FTP command. It can be used as a basic buffer overflow detection.
 number
number
![$\{ cmd [cmd] \}$](img10.png)
This specifies the maximum allowed parameter length for the specified FTP command(s). It can be used as a more specific buffer overflow detection. For example the USER command - usernames may be no longer than 16 bytes, so the appropriate configuration would be:
alt_max_param_len 16 { USER }
![$\{ cmd [cmd] \}$](img10.png)
This option causes a check for string format attacks in the specified commands.
 fmt
fmt 
This option specifies the valid format for parameters of a given command.
fmt must be enclosed in 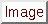 's and may contain the following:
's and may contain the following:
| Value | Description | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| int | Parameter must be an integer | ||||||||||||
| number | Parameter must be an integer between 1 and 255 | ||||||||||||
char  chars chars |
Parameter must be a single character, one of  chars chars |
||||||||||||
date  datefmt datefmt |
Parameter follows format specified, where:
|
||||||||||||
| string | Parameter is a string (effectively unrestricted) | ||||||||||||
| host_port | Parameter must be a host/port specified, per RFC 959 | ||||||||||||
| long_host_port | Parameter must be a long host port specified, per RFC 1639 | ||||||||||||
| extended_host_port | Parameter must be an extended host port specified, per RFC 2428 | ||||||||||||
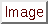 , , 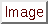 |
One of choices enclosed within, separated by  |
||||||||||||
 , , ![$[]$](img12.png) |
One of the choices enclosed within  , optional value enclosed within , optional value enclosed within ![$[]$](img12.png) |
Examples of the cmd_validity option are shown below. These examples are the default checks, per RFC 959 and others performed by the preprocessor.
cmd_validity MODE <char SBC>
cmd_validity STRU <char FRP>
cmd_validity ALLO < int [ char R int ] >
cmd_validity TYPE < { char AE [ char NTC ] | char I | char L [ number ] } >
cmd_validity PORT < host_port >
A cmd_validity line can be used to override these defaults and/or add a check for other commands.
# This allows additional modes, including mode Z which allows for
# zip-style compression.
cmd_validity MODE < char ASBCZ >
# Allow for a date in the MDTM command.
cmd_validity MDTM < [ date nnnnnnnnnnnnnn[.n[n[n]]] ] string >
MDTM is an off case that is worth discussing. While not part of an established standard, certain FTP servers accept MDTM commands that set the modification time on a file. The most common among servers that do, accept a format using YYYYMMDDHHmmss[.uuu]. Some others accept a format using YYYYMMDDHHmmss[+|-]TZ format. The example above is for the first case (time format as specified in http://www.ietf.org/internet-drafts/draft-ietf-ftpext-mlst-16.txt)
To check validity for a server that uses the TZ format, use the following:
cmd_validity MDTM < [ date nnnnnnnnnnnnnn[{+|-}n[n]] ] string >
 yes
yes no
no
This option turns on detection and alerting when telnet escape sequences are seen on the FTP command channel. Injection of telnet escape sequences could be used as an evasion attempt on an FTP command channel.
 yes|no
yes|no
This option allows Snort to ignore telnet escape sequences for erase character (TNC EAC) and erase line (TNC EAL) when normalizing FTP command channel. Some FTP servers do not process those telnet escape sequences.
This option causes the rest of snort (rules, other preprocessors) to ignore FTP data channel connections. Using this option means that NO INSPECTION other than TCP state will be performed on FTP data transfers. It can be used to improve performance, especially with large file transfers from a trusted source. If your rule set includes virus-type rules, it is recommended that this option not be used.
Use of the "data_chan" option is deprecated in favor of the "ignore_data_chan" option. "data_chan" will be removed in a future release.
 yes
yes no
no
This option causes the rest of Snort (rules, other preprocessors) to ignore FTP data channel connections. Setting this option to "yes" means that NO INSPECTION other than TCP state will be performed on FTP data transfers. It can be used to improve performance, especially with large file transfers from a trusted source. If your rule set includes virus-type rules, it is recommended that this option not be used.